1. 개요
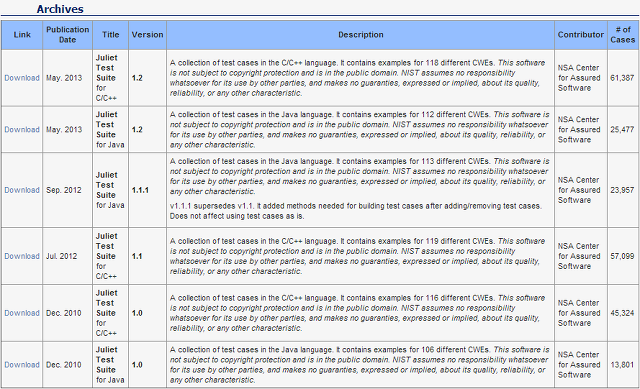
NIST Test Suites는 NIST(미국 국립표준기술연구소)에서 만든 취약한 데이터 셋이다. 해당 데이터셋은 CWE 기준으로 분류되어 있으며, Archives 기준으로 가장 최근 버전은 2013년 5월 1.2 버전이다. 이 Archives 를 Juliet Test Suite 로 불리기도 한다. 해당 버전에는 2 가지 형태로 나눠지는데, C/C++ 버전과 Java 버전으로 나뉘어진다.
이 데이터 셋을 다운로드 받아서 압축을 해제해보면 파이썬으로 관리하는 것을 볼 수 있다. 기회가 되는대로 직접 파이썬을 실행하여 동작을 확인해 보려 한다.
로우한 데이터셋은 testcases 폴더안에 있으며, 각각의 디렉터리에는 다시 세부적으로 폴더로 구분되어 있다. 세부적인 폴더는 단순한 구분을 위해 사용되며, 각 폴더 안에는 bat 파일, 각종 C/C++ 언어 파일, main.cpp, main_linux.cpp, Makefile, testcases.h 파일이 존재한다.
이 Test Suites에 항목화 되어 있는 CWE 리스트는 다음과 같다.
CWE-15 External Control of System or Configuration Setting
CWE-23 Relative Path Traversal
CWE-36 Absolute Path Traversal
CWE-78 Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection')
CWE-90 Improper Neutralization of Special Elements used in an LDAP Query ('LDAP Injection')
CWE-114 Process Control
CWE-121 Stack-based Buffer Overflow
CWE-122 Heap-based Buffer Overflow
CWE-123 Write-what-where Condition
CWE-124 Buffer Underwrite ('Buffer Underflow')
CWE-126 Buffer Over-read
CWE-127 Buffer Under-read
CWE-134 Uncontrolled Format String
CWE-176 Improper Handling of Unicode Encoding
CWE-188 Reliance on Data/Memory Layout
CWE-190 Integer Overflow or Wraparound
CWE-191 Integer Underflow (Wrap or Wraparound)
CWE-194 Unexpected Sign Extension
CWE-195 Signed to Unsigned Conversion Error
CWE-196 Unsigned to Signed Conversion Error
CWE-197 Numeric Truncation Error
CWE-222 Truncation of Security-relevant Information
CWE-223 Omission of Security-relevant Information
CWE-226 Sensitive Information Uncleared Before Release
CWE-242 Use of Inherently Dangerous Function
CWE-244 Improper Clearing of Heap Memory Before Release ('Heap Inspection')
CWE-247 Reliance on DNS Lookups in a Security Decision
CWE-252 Unchecked Return Value
CWE-253 Incorrect Check of Function Return Value
CWE-256 Plaintext Storage of a Password
CWE-259 Use of Hard-coded Password
CWE-272 Least Privilege Violation
CWE-273 Improper Check for Dropped Privileges
CWE-284 Improper Access Control
CWE-319 Cleartext Transmission of Sensitive Information
CWE-321 Use of Hard-coded Cryptographic Key
CWE-325 Missing Required Cryptographic Step
CWE-327 Use of a Broken or Risky Cryptographic Algorithm
CWE-328 Reversible One-Way Hash
CWE-338 Use of Cryptographically Weak PRNG
CWE-364 Signal Handler Race Condition
CWE-366 Race Condition within a Thread
CWE-367 Time-of-check Time-of-use (TOCTOU) Race Condition
CWE-369 Divide By Zero
CWE-377 Insecure Temporary File
CWE-390 Detection of Error Condition Without Action
CWE-391 Unchecked Error Condition
CWE-396 Declaration of Catch for Generic Exception
CWE-397 Declaration of Throws for Generic Exception
CWE-398 Indicator of Poor Code Quality
CWE-400 Uncontrolled Resource Consumption ('Resource Exhaustion')
CWE-401 Improper Release of Memory Before Removing Last Reference ('Memory Leak')
CWE-404 Improper Resource Shutdown or Release
CWE-415 Double Free
CWE-416 Use After Free
CWE-426 Untrusted Search Path
CWE-427 Uncontrolled Search Path Element
CWE-440 Expected Behavior Violation
CWE-457 Use of Uninitialized Variable
CWE-459 Incomplete Cleanup
CWE-464 Addition of Data Structure Sentinel
CWE-467 Use of sizeof() on a Pointer Type
CWE-468 Incorrect Pointer Scaling
CWE-469 Use of Pointer Subtraction to Determine Size
CWE-475 Undefined Behavior For Input to API
CWE-476 NULL Pointer Dereference
CWE-478 Missing Default Case in Switch Statement
CWE-479 Signal Handler Use of a Non-reentrant Function
CWE-480 Use of Incorrect Operator
CWE-481 Assigning instead of Comparing
CWE-482 Comparing instead of Assigning
CWE-483 Incorrect Block Delimitation
CWE-484 Omitted Break Statement in Switch
CWE-500 Public Static Field Not Marked Final
CWE-506 Embedded Malicious Code
CWE-510 Trapdoor
CWE-511 Logic/Time Bomb
CWE-526 Information Exposure Through Environmental Variables
CWE-534 Information Exposure Through Debug Log Files
CWE-535 Information Exposure Through Shell Error Message
CWE-546 Suspicious Comment
CWE-561 Dead Code
CWE-562 Return of Stack Variable Address
CWE-563 Unused Variable
CWE-570 Expression is Always False
CWE-571 Expression is Always True
CWE-587 Assignment of a Fixed Address to a Pointer
CWE-588 Attempt to Access Child of a Non-structure Pointer
CWE-590 Free of Memory not on the Heap
CWE-591 Sensitive Data Storage in Improperly Locked Memory
CWE-605 Multiple Binds to Same Port
CWE-606 Unchecked Input for Loop Condition
CWE-615 Information Exposure Through Comments
CWE-617 Reachable Assertion
CWE-620 Unverified Password Change
CWE-665 Improper Initialization
CWE-666 Operation on Resource in Wrong Phase of Lifetime
CWE-667 Improper Locking
CWE-672 Operation on a Resource after Expiration or Release
CWE-674 Uncontrolled Recursion
CWE-675 Duplicate Operations on Resource
CWE-676 Use of Potentially Dangerous Function
CWE-680 Integer Overflow to Buffer Overflow
CWE-681 Incorrect Conversion between Numeric Types
CWE-685 Function Call With Incorrect Number of Arguments
CWE-688 Function Call With Incorrect Variable or Reference as Argument
CWE-690 Unchecked Return Value to NULL Pointer Dereference
CWE-758 Reliance on Undefined, Unspecified, or Implementation-Defined Behavior
CWE-761 Free of Pointer not at Start of Buffer
CWE-762 Mismatched Memory Management Routines
CWE-773 Missing Reference to Active File Descriptor or Handle
CWE-775 Missing Release of File Descriptor or Handle after Effective Lifetime
CWE-780 Use of RSA Algorithm without OAEP
CWE-785 Use of Path Manipulation Function without Maximum-sized Buffer
CWE-789 Uncontrolled Memory Allocation
CWE-832 Unlock of a Resource that is not Locked
CWE-835 Loop with Unreachable Exit Condition ('Infinite Loop')
CWE-843 Access of Resource Using Incompatible Type ('Type Confusion')
2. 참조
'Information Security > Security Information' 카테고리의 다른 글
| CVE (Common Vulnerabilities and Exposures) (0) | 2015.05.12 |
|---|---|
| 전사적 정보보호 프레임워크에 관한 개인 위키 (0) | 2014.07.14 |
| Honeypot과 Client Honeypot (0) | 2014.01.22 |
| 블랙햇이 사용하는 hanging on 소프트웨어와 MLM 매커니즘 (0) | 2013.10.26 |
| The Chinese Underground. (0) | 2013.10.09 |